AML Solution
Future-proof compliance. AI-powered defense against financial crime.
Financial institutions today are struggling under the weight of excessive false positives, unsustainable scaling costs, and detection systems that are too slow to deploy and too late to act.
Our next-generation AML application is designed to address these core challenges by merging high-performance architecture with intelligent automation.
Challenges for Financial Institutions and Businesses

Inundation with false alarms leads to alarm fatigue, diverting resources and causing operational burnout.

Unreliable or inconsistent detection of suspicious activity

Slow Time-to-Market: Long deployment cycles for model and rule changes (change requests) hinder agility and responsiveness.

The lack of a testing environment (workbench) prevents analysts from quickly testing new detection hypotheses and strategies.

Slow execution of transaction pattern detection logic delays insights and response times.

Unsustainable Costs and Downtime: The cycle of constantly adding more hardware to cope with volume increases costs and introduces system downtime.

Late detection of financial crime risks leads to regulatory exposure and customer dissatisfaction.

Systems struggle to scale effectively to handle the rapidly growing volume of transactions.
Key Differentiators & Capabilities
Agile Rule Creation
Set up simple to complex AML rules in minutes, enabling immediate responsiveness to emerging threats.
Versatile Detection
Leverage a rich library of diverse detection techniques and easily combine multiple techniques for high-precision, layered security.
Hypothesis Validation
Back-test new rules against historical time periods to quickly validate hypotheses and fine-tune effectiveness before deployment.
Reducing False Positives
By focusing on behavior rather than relying solely on signatures or rules, behavioral analytics can reduce the number of false positives generated by security systems, allowing security teams to prioritize real threats.
Customized Filtering
Effortlessly manage your own watch lists and whitelists for granular control, minimizing false positives and focusing analyst efforts.
Explainable Anomalies (XAI)
Access fully explainable anomalies providing clear context and rationale behind every alert to satisfy auditors and build analyst trust.
Performance & Architectural Advantage
Massive Volume Handling
Effortlessly scale to process a billion transactions a day or more, future-proofing your operations against rapid data growth.
Hardware Efficiency
Built using high-performance languages (e.g., C++), the application extracts maximum efficiency from existing hardware, reducing the need for costly infrastructure upgrades.
Simplified Deployment
Enjoy simple deployment and the flexibility to scale out capacity exactly when and where necessary.
Anomalies
Provides a real-time feed of confirmed anomalies directly to downstream applications, enabling immediate action and response.
Trigger Callback
Trigger callback actions to instantly notify and integrate with external tools (e.g., case management systems, regulatory reporting platforms).
Low Total Cost of Ownership (TCO)
Optimized architecture and high efficiency lead to a significantly low cost of maintenance and operations.
Link Analysis & Network
Exploration

Interactive Network Exploration: Visually explore and manipulate interactive transaction network graphs to quickly identify key entities and relationships.

Time-Sliced Analysis: Slice the network based on a specific date range to analyze transactional behavior over discrete periods, pinpointing when suspicious activity occurred.

Advanced Pattern Detection: Automatically identify key network structures like high-density communities and suspicious transactional triangles.

Relationship Tracing: Instantly find and trace all transaction paths between any two parties, revealing the complete flow of funds.

Contextual Profiling: Gain deeper insights by profiling network activity based on sender and receiver characteristics (e.g., transaction history, geography, associated risk score).

Dynamic Network Intelligence: Incrementally build and update the transaction graph in real-time as new data arrives, providing analysts with an always-current, accurate view of financial networks.
Investigation & Advanced Analysis
 Intuitive Data Exploration: Use interactive graphical tools to efficiently explore and summarize data, and easily drill down to the fine-grain details required for accurate decision-making.
Intuitive Data Exploration: Use interactive graphical tools to efficiently explore and summarize data, and easily drill down to the fine-grain details required for accurate decision-making. Flexible Ad-Hoc Analysis: Perform immediate, ad-hoc analysis using a no-code query builder or direct SQL access for power users.
Flexible Ad-Hoc Analysis: Perform immediate, ad-hoc analysis using a no-code query builder or direct SQL access for power users. API-Driven Insights: Leverage a comprehensive API for deeper analytical workflows and custom model development using Python or other preferred tools.
API-Driven Insights: Leverage a comprehensive API for deeper analytical workflows and custom model development using Python or other preferred tools. Data Archiving & Analytics: Utilize built-in connectors to data lakes for seamless data archiving, regulatory compliance, and enabling advanced big data analytics.
Data Archiving & Analytics: Utilize built-in connectors to data lakes for seamless data archiving, regulatory compliance, and enabling advanced big data analytics. Integrated Case Management: Features built-in case management to streamline alert review, collaboration, regulatory filing, and end-to-end investigation processes.
Integrated Case Management: Features built-in case management to streamline alert review, collaboration, regulatory filing, and end-to-end investigation processes.
Machine Learning
 Dynamic Risk Segmentation: Create and maintain dynamic customer segmentation for precise, risk- based scoring, moving beyond generic AML profiles.
Dynamic Risk Segmentation: Create and maintain dynamic customer segmentation for precise, risk- based scoring, moving beyond generic AML profiles. Intelligent Behavioral Profiling: Build continuous behavioral profiles for all entities, enabling real - time pattern analysis and reliable anomaly detection against established norms.
Intelligent Behavioral Profiling: Build continuous behavioral profiles for all entities, enabling real - time pattern analysis and reliable anomaly detection against established norms. Continuous Optimization: Perform continuous, automated assessment of rule and model effectiveness, ensuring your defenses are always optimized against evolving threats and minimizing false positives.
Continuous Optimization: Perform continuous, automated assessment of rule and model effectiveness, ensuring your defenses are always optimized against evolving threats and minimizing false positives. Extract critical insights using sophisticated text mining capabilities.
Extract critical insights using sophisticated text mining capabilities.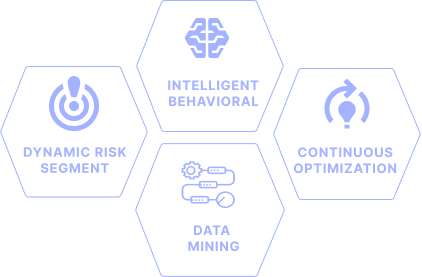
Business Outcomes & Strategic Value
 Actionable Reporting & Insights: Access comprehensive, out-of-the-box reports and dashboards that provide immediate visibility into risk exposure, operational efficiency, and performance metrics.
Actionable Reporting & Insights: Access comprehensive, out-of-the-box reports and dashboards that provide immediate visibility into risk exposure, operational efficiency, and performance metrics. Enhanced Compliance & Auditing: Achieve enhanced regulatory compliance through robust, auditable processes, and transparent reporting capabilities, significantly reducing regulatory risk and penalties.
Enhanced Compliance & Auditing: Achieve enhanced regulatory compliance through robust, auditable processes, and transparent reporting capabilities, significantly reducing regulatory risk and penalties. Comprehensive Risk Mitigation: Ensure comprehensive financial crime detection and proactive risk mitigation across all business lines, protecting institutional integrity and assets.
Comprehensive Risk Mitigation: Ensure comprehensive financial crime detection and proactive risk mitigation across all business lines, protecting institutional integrity and assets. Operational Excellence: Drive streamlined operations and efficiency by automating manual tasks, reducing false positives, and accelerating investigation cycles.
Operational Excellence: Drive streamlined operations and efficiency by automating manual tasks, reducing false positives, and accelerating investigation cycles. Strategic Business Enablement: Generate strategic business value by turning compliance from a cost center into an enabler of safe, responsible growth and a source of competitive advantage.
Strategic Business Enablement: Generate strategic business value by turning compliance from a cost center into an enabler of safe, responsible growth and a source of competitive advantage.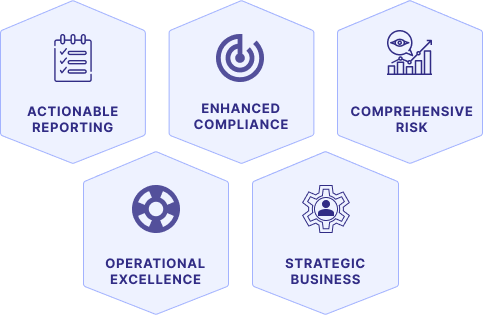
Security, Governance, & Auditing
 Granular Access Control: Ensure strict User Access Management using roles, groups, and user hierarchy to precisely control who can view and interact with sensitive data.
Granular Access Control: Ensure strict User Access Management using roles, groups, and user hierarchy to precisely control who can view and interact with sensitive data. Role-Based Security: Enforce Role-Based Access Control (RBAC) to ensure users only have the permissions necessary for their assigned duties, minimizing internal risk.
Role-Based Security: Enforce Role-Based Access Control (RBAC) to ensure users only have the permissions necessary for their assigned duties, minimizing internal risk. Secure Communications: Protect data integrity and privacy with encrypted traffic across all application components and user access points.
Secure Communications: Protect data integrity and privacy with encrypted traffic across all application components and user access points. Comprehensive Auditability: Maintain complete transparency and regulatory readiness with detailed login history and user activity logs, alongside audit trails for all application configurations and changes.
Comprehensive Auditability: Maintain complete transparency and regulatory readiness with detailed login history and user activity logs, alongside audit trails for all application configurations and changes. Data Protection: Utilize integrated encryption and/or masking features to protect sensitive information (e.g., PII, account numbers) throughout the system, ensuring data privacy and compliance.
Data Protection: Utilize integrated encryption and/or masking features to protect sensitive information (e.g., PII, account numbers) throughout the system, ensuring data privacy and compliance.
Looking to secure your data to detect threats in real-time?
Our solutions provide an exceptional out-of-the-box experience designed for rapid deployment and actionable insights.
GET IN TOUCH